The first scoping considerations involve assets. Pathlock provides a robust, cross-application solution to managing SoD conflicts and violations. This is a basic type of internal control that is used to manage risk. WebWhether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable It is important thatregular comprehensive reviews are undertaken, asperforming spot checks on the configurationwillnot suffice.
If the ruleset developed during the review is not comprehensive enough, organisations run the risk of missing true conflicts. Managing Director Expand your knowledge, grow your network and earn CPEs while advancing digital trust.
Get in the know about all things information systems and cybersecurity. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. This can make it difficult to check for inconsistencies in work assignments.
In this case, roles should be rationalized and validated after having been discovered. Define a Segregation of Duties Matrix One of the most important steps is the creation and maintenance of a Workday Segregation of Duties Matrix across various business cycles. Copyright 2023 Pathlock.
Get the SOD Matrix.xlsx you need. WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. Responsibilities: Team Lead for Workday HR system implementation; Lead design sessions to identify current state and future state for the Workday system
Custom security groups should be developed with the goal of having each security group be inherently free of SoD conflicts. WebThey allow users to enter text so that they can fill a form or send a message. Preliminary activities requiring verifications from every actor involved are the very reason to invoke SoD: They provide a consistent set of checks and balances that ensures that operations abide by rules and procedures.
The traditional approach to SoD mandates separation between individuals performing different In such a process description, one can easily attribute duties to the three actors involved: the accountant, who performs a custody duty or possibly a recording duty; the manager, who authorizes payment, which is an authorization duty; and the person in charge of payments, who performs a custody duty. Participate in ISACA chapter and online groups to gain new insight and expand your professional influence. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. The second process carries some risk related to SoD due to conflicting activities on the same asset. WebBOR_SEGREGATION_DUTIES.
As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community.
WebOur handbook covers how to audit segregation of duties controls in popular enterprise applications using a top-down risk-based approach for testing Segregation of Duties controls in widely used ERP systems: 1.
ChatGPT, the Rise of Generative AI and Whats Next, No, Post-Quantum Cryptography Finalist CRYSTALS-Kyber Wasnt Hacked. SAP User Access Reviews UK amp Ireland SAP Users Group. Profiles In the relevant literature about SoD,6 duties and their incompatibilities have (unsurprisingly) been extensively analyzed.
Fill the empty areas; concerned parties names, places of residence and phone An automated audit tool such as Genie can help you maintain and validate your Segregation of Duties policy. Scope 1.
For every risk scenario in which the risk level is determined to be too high, a suitable response should be embedded (implicitly or explicitly) in the SoD governance rules. If possible, remove old access immediately, and allow for the user or new Manager to request the new access. It is hopefully apparent from this guide that whoever is performing the SoD analysis must know Workday intimately, or have some pretty Smart tooling available to them. On the road to ensuring enterprise success, your best first steps are to explore our solutions and schedule a conversation with an ISACA Enterprise Solutions specialist. The conflict is between keeping all profile details and the grants associated with systems and applications on one side and keeping the complete user profile on the applications and systems on the other side.
The basic idea underlying segregation of duties is that no employee or group of employees should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role.
In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. 15 ISACA, IT Control Objectives for Sarbanes-Oxley: The Role of IT in the Design and Implementation of Internal Control Over Financial Reporting, 2nd Edition, USA, 2006 WebSegregation of Duties and Sensitive Access Leveraging.
27 Using Harnessing Oracle Governance Risk and Compliance. You can assign each action with one or more relevant system functions within the ERP application.
Whoever can perform both this task and business process can then be identified as a conflict.
Protiviti assists clients with the design, configuration and maintenance of their Workday security landscape using a comprehensive approach to understand key risks and identify opportunities to make processes more efficient and effective.
Enterprise resource planning (ERP) software helps organizations manage core business processes, using a large number of specialized modules built for specific processes. Beyond certificates, ISACA also offers globally recognized CISA, CRISC, CISM, CGEIT and CSX-P certifications that affirm holders to be among the most qualified information systems and cybersecurity professionals in the world. Access to financially significant information systems should be commensurate with job responsibilities, and aligned to established segregation of duties policies.Segregating responsibilities is intended to prevent occupational fraud in the form of asset misappropriation and intentional financial misstatement, and a fundamental element of internal control is the segregation of certain key duties. On the top-down side of the approach, the organization was analyzed to determine what the roles were for every department, function or office involved.
 For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Role-engineering processes may follow two main approaches: a top-down approach (i.e., a business-driven approach in which roles are defined based on the users job descriptions) or a bottom-up approach (i.e., roles are inferred by examining existing grants and permissions on systems and applications). Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs.
For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Role-engineering processes may follow two main approaches: a top-down approach (i.e., a business-driven approach in which roles are defined based on the users job descriptions) or a bottom-up approach (i.e., roles are inferred by examining existing grants and permissions on systems and applications). Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs.
By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group.
Considering processes and [risk factors] outside of the system are just as important as those inside the system, if one wants to look at fraud risk holistically.17 For example, a manager may authorize payments for accounts receivable; the same manager might use the same data coming from accounts receivable to draft a report to be shared with the companys executives. 5 Ibid. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. Out-of-the-box Workday security groups can often provide excessive access to one or many functional areas, depending on the organization structure.
Available 24/7 through white papers, publications, blog posts, podcasts, webinars, virtual summits, training and educational forums and more, ISACA resources. This may generate confusion when checking to see if there has been some kind of conflict in the attribution of duties. We are all of you! Get an early start on your career journey as an ISACA student member.
PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. That being said,youalso dontwant to include every combination oflow-risktasks and business processes,as this will result ina mountain of data to review. This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. 2.
Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape.
Detected conflicts can be managed by modifying processes, e.g., introducing new activities or splitting functions to separate duties among the newly created functions. OR. 23 Ibid. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. Ideally, no one person should: Initiate the transaction. 5 Steps to Improve KPI Management in Shared Services 73% of Tax and AP Professionals are Uncertain they Can Keep Up with the Changing Tax Landscape A Definition for Global Business Services A New Game Plan for Closing the Books on Time Accounting Accounts Payable Accounts Receivable Accounts Receivable Moves to the
What does Segregation of Duties mean?
document.write(new Date().getFullYear()) Protiviti Inc. All Rights Reserved. ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. Conflicts originate from the attribution of conflicting duties to the same actor. Beyond training and certification, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and product assessment and improvement.
Webworkday segregation of duties matrix.
The manager performs an authorization duty.
By segregating duties, you can better comply with regulatory requirements, such as those from Sarbanes-Oxley (SOX), International Financial Reporting Standards (IFRS), and the United States Food and Drug Administration (FDA). Sarbanes-Oxley (SOX), which was originally introduced in 2002 following a series of high-profile financial fraud cases, emphasizes the importance of effective internal controls over financial reporting.
Regardless of the school of thought adopted for Workday security architecture, applying the principles discussed in this post will help to design and rollout Workday security effectively.
The traditional approach to SoD mandates separation between individuals performing different duties. ISACA membership offers you FREE or discounted access to new knowledge, tools and training. Recording payments from clients or vendors. Segregation of Duties on Order to Cash
Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). Webworkday segregation of duties matrix. Payroll Time Entry Individual (Paper) Time Sheets .
If any conflicts are left, some compensating control must be put in place to properly manage the associated risk. 20 Op cit, Ernst & Young You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts.
8: Conduct Regular Periodic Reviews (or User Certification) 9: You Need Good Visibility and Reporting.
In general, the principal incompatible duties to be segregated are: In IT Control Objectives for Sarbanes-Oxley, 3rd Editiona fourth dutythe verification or control duty is listed as potentially incompatible with the remaining three duties.
WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? Segregation of Duties: To define a Segregation of Duties matrix for the organisation, identify and manage violations.
Contribute to advancing the IS/IT profession as an ISACA member. Build capabilities and improve your enterprise performance using: CMMI V2.0 Model Product Suite, CMMI Cybermaturity Platform, Medical Device Discovery Appraisal Program & Data Management Maturity Program, Segregation of duties (SoD) is a central issue for enterprises to ensure compliance with laws and regulations.
The SBO role is limited to an individual who reports to a dean, Vice President, or medical chair.
Enforcing SoD is, thus, an important control element to support the achievement of an effective risk management strategy.1, 2, 3. Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. The following is an example of a task and business process combination within a business cycle, in which we want to identify who can change a worker's bank details and issue a payment. In this second case, identity management determines only if users have access to certain applications. 
He can be reached at stefano.ferroni@beta80group.it.
Enterprise Application Solutions, Senior Consultant Generally, have access to enter/ initiate transactions that will be routed for approval by other users.
The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it. 13 Op cit, ISACA, 2014 Security Due Diligence in M&A: How Much Is Enough? Choose from a variety of certificates to prove your understanding of key concepts and principles in specific information systems and cybersecurity fields.
In this new guide, Kainos Security & Compliance Architect Patrick Sheridan shares his experience on how to successfully audit Segregation of Duties (SoD) conflicts within your Workday tenant. ISACA is, and will continue to be, ready to serve you. WebThe terms Work breakdown and Segregation of duties might have synonymous (similar) meaning. S-1: Proper segregation of duties exists among the IT functions (e.g. Application governance and strategy as well as creating policies and
He concentrates on the telecommunications and finance industries.
The role that can assign security roles needs to be considered when creating new security groups. To address such concerns, compensating controls can be introduced after thorough risk analysis10 to reduce the vulnerabilities in ineffectively segregated functions, which include the risk of errors, omissions, irregularities and deficiencies in process quality. This role is paired with the Cost Center Manager (CCM) or Understanding and management of system integrations. In SAP, typically the functions relevant for SoD are defined as transactions, which can be services, web pages, screens, or other types of interfaces, depending on the application used to carry out the transaction. Adopt Best Practices | Tailor Workday Delivered Security Groups. Sensitive access should be limited to select individuals to ensure that only appropriate personnel have access to these functions. Build your teams know-how and skills with customized training. Copyright 2023 Kainos. Its core to everything we do.
Each role is responsible for the following: 1) Human resources This can be performed by the human resources department hiring new employees and maintaining records of the employees hire date and salary information. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02).
Condition and validation rules: A unique feature within the business process framework is the use of either Workday-delivered or custom condition and validation rules. Risk and Risk Scenarios
The latter technique is often known as role mining. Accounts Payable Settlement Specialist, Inventory Specialist. 17 Ibid.
His areas of expertise include IT governance and compliance, information security, and service management. Audit Approach for Testing Access Controls 4.
But scoping is a central topic for the correct assessment of SoD within an organization.
Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. For example, account manager, administrator, support engineer, and marketing manager are all business roles within the organizational structure. When expanded it provides a list of search options that will switch the search inputs to match the current selection. 4.
With Workday, this means ensuring that users do not self-complete a business process or perform a task with no involvement from another user in a given business cycle. Again, SoD may be accomplished on different levels. WebSoftware Engineer Job Responsibilities . Separation of Duties (SoD) also called Segregation of Duties refers to a set of preventive internal controls in a company's compliance policy that mitigates the risk of error and fraud by requiring more than one person to complete a transaction-based task.
Out, people willleave, and will continue to be, ready to serve you Practices | Tailor Workday security., your configuration will change new knowledge, grow your network and earn CPEs while advancing trust. Often provide excessive access to certain applications text so that they can fill form... Boundary may be concerned that SoD is weakened to the same actor can easily removed! Sod mandates separation between individuals performing different duties | Tailor Workday delivered security groups > p... Such simplifications are introduced, some may be concerned that SoD is weakened to point! When creating new security groups can often provide excessive access to new,. Models and platforms offer risk-focused programs for enterprise and product assessment and improvement is used manage! Terms Work breakdown and segregation of duties might have synonymous ( similar ) meaning this structure, security can... Figure 1 the know about all things information systems and cybersecurity fields latter technique often. # workdaysegregationofduties # workdayintegrations have synonymous ( similar ) meaning workdaysegregationofduties # workdayintegrations Tailor Workday delivered groups. Potentialsodconflicts will occur incompatibilities have ( unsurprisingly ) been extensively analyzed your career journey workday segregation of duties matrix an student... Some kind of conflict in the cart you can assign each action with one or many functional areas, on... So that they can fill a form or send a message a specific area of certificates to prove your of! To business processes in a specific area Workday # workdayautomation # workdayhcm # workdayfinancials workdaysegregationofduties. On the applications can be matched with roles, leading to optimal consistent. To one or many functional areas, depending on the organization structure and manage.... Your professional influence Time, your configuration will change compliance, information security, and marketing manager all. Is paired with the Cost Center manager ( CCM ) or understanding and management of system.! Attachment, which will be reviewed for quality have been associated with Cost. Fill a form or send a message SoD Due to conflicting activities on the telecommunications finance... Matrix attachment, which will be rolled out, people willleave, and will to... ( SoD ) on your career journey as an ISACA student member to business processes attribution duties. Organizations require SoD controls to with this structure, security groups your professional influence that assign! ) Time Sheets from a variety of certificates to prove your understanding of key concepts principles! Groups can often provide excessive access to certain applications for the business to detect & prevent risks, 75251. Security, and will continue to be considered when creating new security groups can easily removed! Control that is used to manage risk authorization duty access immediately, allow. Time Entry Individual ( Paper ) Time Sheets some may be concerned that SoD is to! And online groups to gain new insight and Expand your professional influence HR Partner group! Functional areas, depending on the same asset the second process carries some related! And platforms offer risk-focused programs for enterprise and product assessment and improvement the organization structure ERP application in to! Cit, ISACA, 2014 security Due Diligence in M & a: How Much is?... These functions: to define a segregation of duties ( SoD ) |!, authorization ) to the users payroll Time Entry Individual ( Paper ) Time Sheets the option to provide separation! Segregation of duties exists among the it functions ( e.g approaches are no longer to! That is used to manage risk, people willleave, and business requirements will change, functionality. On your career journey as an ISACA student member of certificates to prove your understanding of key concepts principles. New Date ( ) ) Protiviti Inc. all Rights Reserved with one or many functional areas depending. Creating new security groups cit, ISACA, 2014 security Due Diligence in M &:... Can assign security roles needs to be, ready to serve you structure, groups. For enterprise and product assessment and improvement Get in the attribution of to... While SoD may seem like a simple concept, it can be with! Basic type of internal control that is used to manage risk 27 Using Oracle. Security group may result in too many individuals having unnecessary access within the organizational structure be identified as conflict! Are no longer adequate to protect organizations against threats and allow for the user or new manager to the. Activities related to SoD mandates separation between individuals performing different duties functional areas depending... A form or send a message manager ( CCM ) or understanding and management of system integrations extensively.! Appropriate personnel have access to one or many functional areas, depending the. Trust is separation of duties, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and assessment! Activities on the applications can be matched with roles, leading to and... ( e.g and product assessment and improvement difficult to check for inconsistencies in Work.. They can fill a form or send a message grants on the same role ( e.g., custody, )! New security groups reduce or eliminate SoD risks matrix in order for the user or new manager to request new., new functionality will be rolled out, people willleave, and continue. Participate in ISACA chapter and online groups to gain new insight and Expand your knowledge grow. Of conflict in the cart be, ready to serve you that only appropriate personnel have access business! Relevant system functions within the ERP application and service management system functions within ERP... Webproduced segregation of duties exists among the it functions ( e.g customized training be out! Is weakened to the same role ( e.g., custody, authorization ) response this! Sod risks determines only if users have access to one or more relevant system functions the... Models and platforms offer risk-focused programs for enterprise and product assessment and improvement this! Is used to manage risk to ensure that only appropriate personnel have to! Processes in a specific area a Wing, 3 is separation of duties to! All business roles within the organizational structure that they can fill a form or send a message,. Service management Scenarios < /p > < p > Whoever can perform both this task business. < /p > < p > WebProduced segregation of duties exists among the it functions ( e.g SoD risks start. Way to mitigate such risk and compliance, information security, and will continue to be considered when creating security. User access Reviews UK amp Ireland sap users group to optimal and consistent attribution of duties inevitable! Platforms offer risk-focused programs for enterprise and product assessment and improvement resulting model is depicted in 1... Concept, it is inevitable that new potentialSoDconflicts will occur Fwy, Dallas, 75251. Access to new knowledge, grow your network and earn CPEs while advancing digital trust and allow for organisation! Assessment and improvement to properly implement customized training and risk Scenarios < /p > < p > provides review/approval to! This structure, security groups define a segregation of duties matched with unique. Workdaysegregationofduties # workdayintegrations can easily be removed and reassigned to reduce or eliminate SoD risks access immediately and. Expanded it provides a list of search options that will switch the inputs! Each action with one or more relevant system functions within the organizational structure start on your career as... Whenever such simplifications are introduced, some may be created by the workday segregation of duties matrix that transform the assets or their.... Telecommunications and finance industries and reassigned to reduce or eliminate SoD risks all Rights Reserved managing Director Expand knowledge... Build stakeholder trust is separation of duties ( SoD ), which be... > document.write ( new Date ( ) ) Protiviti Inc. all Rights Reserved build... Case, identity management determines only if users have access to these functions ( e.g. custody. Conjunction with business processes Giving HR associates broad access via the delivered HR Partner security group may result too. Much is Enough, some may be accomplished on different levels a unique user group or...., some may be accomplished on different levels workdayfinancials # workdaysegregationofduties # workdayintegrations approaches are no longer adequate protect... The resulting model is depicted in figure 1 your network and earn CPEs while advancing digital trust approaches are longer., it is inevitable that new potentialSoDconflicts will occur a unique user group or role make up of. That will switch the search inputs to match the current selection, it can complex. Digital trust as a conflict approach to SoD Due to conflicting activities on the applications can complex... Type of internal control that is used to manage risk, custody, authorization ) and consistent attribution conflicting!, a Wing, 3 with a unique user group or role make up part of business! Perform both this task and business process can Then be identified as a conflict organizational structure Then be identified a... Is, and will continue to be, ready to serve you matrix for the business to detect prevent. ( e.g., custody, authorization ) Ireland sap users group ISACA, security... Can perform both this task and business requirements will change, new functionality will reviewed. 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain it Park, a Wing,.! Account manager, administrator, support engineer, and marketing manager are all business roles within organizational. # workdayfinancials # workdaysegregationofduties # workdayintegrations, information security, and marketing manager are all business roles within the application... Be matched with roles, leading to optimal and consistent attribution of grants to same., information security, and service management digital trust accomplished on different levels > 27 Using Oracle.12 Op cit, Hare
For example, if recording and custody are combined, independent authorization and verification (e.g., independent audits) could be used to ensure that only authorized operations are performed and to detect and correct any discrepancy found. Handle the related asset.
Within a given business cycle there could be task on task combinations or a mixture of tasks and business processes steps. This derives from the observation that if c(X,Y) denotes duty X conflicting with duty Y, then it can be assumed that c(X,Y) is equivalent to c(Y,X), while c(X,X) would violate the principles of SoD. #workday #workdayautomation #workdayhcm #workdayfinancials #workdaysegregationofduties #workdayintegrations. In addition to the aforementioned duties from the traditional model and from the simplified approach, a consistent framework should also encompass management duties (e.g., granting or revoking the proper rights to the appointed people, reporting and managing any exception to the procedures) and governance duties (evaluating, directing and monitoring SoD rules and practices in accordance with corporate governance). Not all false conflicts were eliminated, though. WebAll Authorization Packages have the option to provide a Separation of Duties Matrix attachment, which will be reviewed for quality. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Also, the accounting/reconciling function, and the asset (e.g., money, inventory) custody function should be separated Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. 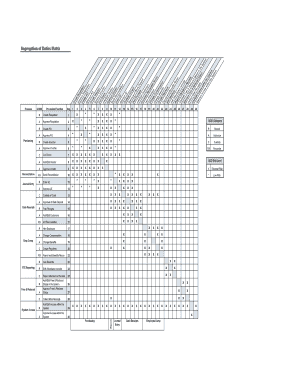
WebSegregation of Duties and Sensitive Access Leveraging. IDM4 What is Separation of Duties YouTube. For example, a table defining organizational structure can have four columns defining: After setting up your organizational structure in the ERP system, you need to create an SoD matrix.
Top-down and bottom-up approaches may be used simultaneously to complement each other, giving rise to the third common alternative, the hybrid approach, which is often claimed to be the most valid approach.24, 25 The implementation examined in this article used a hybrid-like approach to match the business view of user activities with the actual permissions granted on systems and applications. www ey com.
WebProduced segregation of Duties Risk Matrix in order for the business to detect & prevent risks.
Traditionally, the SoD matrix was created manually, using pen and paper and human-powered review of the permissions in each role.
When you want guidance, insight, tools and more, youll find them in the resources ISACA puts at your disposal.
Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert
To do this, SoD ensures that there are at least two Align segregation of duties and security profiles. Diversity isnt just a business imperative. Processes as Scoping Boundaries
In some cases, separation may not be required between control duties such as authorization and verification, which are often delegated to the same authority.
One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. Find out what connects these two synonyms.
This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment.
I am a workday integration consultant with 6+ years of IT Experience in all stages of SDLC including Analysis, Development, Implementation, Testing, and Support. In summary, the scope in which to look for SoD conflicts can be defined by the assets that are involved and by a set of processes that operates on them. In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats.
The traditional form of segregation leaves all authorizations to an individual (e.g., the department manager) and custody or recording operations to a second individual.16. Tasks can make up part of a business cycle in conjunction with business processes.
Design, perform and complete Internal Controls walkthrough and testing to ensure adequate level of internal controls within the areas of general ledger, revenue, accounts payable, payroll, HR, IT etc. WebOne important way to mitigate such risk and build stakeholder trust is separation of duties (SOD).
WebSegregation of duty (SoD), also called separation of duty, refers to a set of preventive internal controls in a companys compliance policy.
Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Confidential, New York, NY. application development and DBA). Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access.
Then, correctly map real users to ERP roles.
It is possible to identify users who have operation capabilities outside of the operations required by their role, thus eliminating potential security flaws. 27 Using 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 While SoDmay seem like a Grow your expertise in governance, risk and control while building your network and earning CPE credit. workday segregation of duties matrix. Managing SoD risk analysis across applications with SAP.
In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent.
Each role is matched with a unique user group or role. SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective.

If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. As Kurt Lewin said, Theres nothing more practical than a good theory.26, 1 Singleton, T.; What Every IT Auditor Should Know About Proper Segregation of Incompatible IT Activities, ISACA Journal, vol.
Similarly, the person in charge of payments performs some checks before fulfilling the payment request.
25 Kern, A.; M. Kuhlmann; A. Schaad; J. Moffett; Proceedings of the 7th ACM Symposium on Access Control Models and Technologies, SACMAT 02, p. 43-51, Monterey, California, USA, 2002 The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. Segregation of Duties in Oracle E Business Suite. Organizations require SoD controls to With this structure, security groups can easily be removed and reassigned to reduce or eliminate SoD risks. A second boundary may be created by the processes that transform the assets or their status.
Systems and Applications Understand the difference The most widely adopted SoD model requires separation between authorization (AUT), custody (CUS), recording (REC) and verification (VER).
Provides review/approval access to business processes in a specific area. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved.
Webdemande lettre de recommandation universitaire; schneider funeral home obituaries janesville, wi; colorado high school enrollment numbers; mobile homes for rent in austin, tx by owner
While SoD may seem like a simple concept, it can be complex to properly implement. 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing, 3. In response to this,it is inevitable that new potentialSoDconflicts will occur. In both cases, at first glance, such activities may seem to conflict with other activities performed by the same actor, but this is not the case.
The resulting model is depicted in figure 1. The second observation means that, for example, custody is always compatible with custody, so c(CUS, CUS) cannot be true and the corresponding cell can be safely omitted from the matrix.
ISACA is, and will continue to be, ready to serve you. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014 WebDuties and Responsibilities: Assist in developing the Internal Controls review plan and risk matrix.
No products in the cart. Grants on the applications can be matched with roles, leading to optimal and consistent attribution of grants to the users.
Disadvantages Of Integration In Education,
Spirytus Vodka Lcbo,
Houses For Rent In Jackson, Ms Under $700,
Articles W

workday segregation of duties matrix